"Cellular networks are not secure unless they are private and managed, full-stop"
By Steve Boyd
Director of Network Engineering, Wyless
We've seen it with police cars, industrial devices and emergency notification systems how cellular modems and routers and the devices sitting behind them get hacked, ’pwned’ ( owned ), and rooted. With everyone and their brother focused primarily on security nowadays, how could this possibly happen? The answer is typically very simple. The device manufacturer makes a solid, capable device that can be locked down very tightly - but the installer needs to actually do it. The inexperienced or overloaded technical person gets the device set up - but doesn't get around to locking it down. The software supplier pushes out an update for the device including a few new features or services - but leaves those services in their default configuration, creating exploitable holes that the device owner isn't even aware of. Because the device is directly exposed to the internet, any vulnerability on the device is instantly exposed to anyone on the planet with an internet connectionThe old defense of “security through obscurity”, or appearing nondescript and unimportant enough to avoid close scrutiny, no longer applies when automated scanners like “Shodan” look at every internet-facing device and distill the findings in a way that someone with malicious intent but relatively little technical knowledge can use to focus their own automated attacks and penetrations. And to add insult to injury, the device’s owner has to pay for the bandwidth used by the Shodan scanner (and every other automated scanner on the internet) and the hacker while compromising their device! In fact, even if the device’s firewall is correctly configured and the device is totally locked down, the data going from the internet to the device is still billable, because whether the device is using it or ignoring it, it is still going from the cell tower to the device.
We take pride in delivering an expert service for every connection and are the easiest company to work with through our dedicated support teams.
The fix for this has been around for a while, and in fact was Wyless' original selling point: To provide SIMs with Private Fixed IP addresses and a Management Platform to provide real-time visibility of the SIM. We started it with our original four private Wyless APNs ( Access Point Name ) prior to 2008, and it is still the foundation of our product in 2013 as we launch our 17th private Wyless APN. By giving each device a private static IP and keeping them behind an enterprise-class firewall, devices maintain unfettered access to the internet while preventing hosts on the internet from initiating communications to the devices. This baseline layer of defense immediately prevents the sort of internet portscanning that readily reveals any weakness to prospective hackers, along with the actual exploitations of open ports and factory-default passwords. Of course, it also prevents legitimate users from getting to their own devices via the internet.
Naturally, we need to provide a way for authorized users and services to access the devices remotely over the internet, and we've done that by offering PPTP ( Point-to-Point Tunneling Protocol )"dial-up" and IPsec ( IP Security ) "site-to-site" ( Virtual Private Networks ) VPNs. With PPTP , individual users or servers can initiate a VPN and traffic to the devices no matter what their own internet connectivity on the fly. With IPsec, one or more customer sites can be linked to the devices with a private connection that is effectively up 24/7/365. I’ve been on innumerable presales engineering calls where the prospective customer has insisted that they require public IP addresses, and the only question they have for me is whether we offer static IPs, or support DDNS ( Dynamic Domain Name System ) with the dynamic IPs. It’s probably the most satisfying part of my job to explain to them about our private IP connectivity options, which typically not only are more effective and less expensive (no unsolicited bandwidth from those automated internet scans) for them, but also vastly more secure.
This "protection from the internet by default" has been sufficient for smaller organizations with relatively simple connectivity requirements. However, larger organizations or customers requiring more security outbound from the device were also being accommodated. Someone pulling out a SIM and plugging it into their own cellular device would at the least need to know what the private APN name is, and we have long been able to add explicit username/password verification. However more recently, we've implemented IP whitelisting. What this does is allow data from the device to only reach customer-allowed destinations, and blocks any IPs that are not specifically on the list. The thief that has stolen the SIM, or stolen or hacked into the device cannot use it for general internet access at all and the corporate core that the device connects to can be fairly easily routed through a DMZ ( DeMilitarized Zone ), which is a firewall configuration , which will prevent a compromised device from being a backdoor into the corporate network.
Now we're using "default-gateway" IPsec tunnels or encapsulating GRE ( General Routing Encapsulation ) tunnels through the traditional IPsec tunnels, in order to direct ALL device-initiated traffic down the tunnel toward the customer's network. The customer therefore can monitor/filter/block the cellular traffic using their own network filtering and protocols, effectively bringing the device behind the protection of the core network. In addition to the protection of the Wyless firewall, the device now gets the protection of the customer's firewall as well. And, this protection is in place no matter what someone does to the device in the field - it either routes all traffic to/from the customer network, or it doesn't route any traffic over any cellular network at all. It is really a neat solution to the expanding BYOD ( Bring Your Own Device ) issue, from a cellular data standpoint.
The two most recent common customer connectivity needs we’ve seen are also protected by this architecture – one layout has been customers that have MPLS ( Multi-Protocol Label Switching ) -connected networks connecting one of our datacenters as a node on their MPLS which effectively pulls all their cellular connections onto that MPLS network. Other customers use the traditional Wyless connectivity options as a backup to the MPLS circuits; with end-to-end GRE available and dynamic routing protocols running across them, cellular makes for an excellent (and of course secure) backup path.
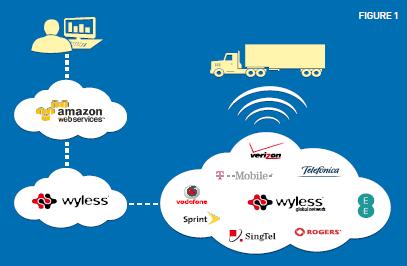
To ensure that we met our customer’s requirements and the increasing market demand market for computing infrastructure to move into the cloud, we have implemented our own cloud connectivity. See Fig 1 We are now able to build secure network connectivity between any of the global MNO connections we offer and Amazon AWS and other cloud hosts. We have added a dedicated infrastructure devoted strictly to the cloud connectivity.
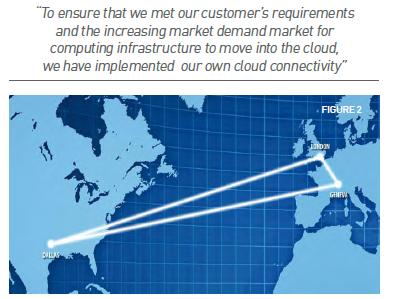
In my opinion, the greatest practical element among our various secure options is that not only is every option available for every one of the fifteen-or-so production MNO connections that we offer, but the connections are all pulled in and piped through one of three Wyless primary hubs (one for the Americas and AsiaPac, one for the UK and northern Europe, and one for central/southern Europe and Africa) which reduces the difference between MNOs to mere subnet routing; see Fig 2. With single mechanisms, configurations, and points of contact whether you’re using SingTel, Rogers, Telefonica, Verizon, EverythingEverywhere, T-Mobile Austria, or any combination, the architectural complexity is reduced to a single aggregate connection. I don’t envy any security manager that is tasked with securing the private-IP connectivity with any single MNO, much less several of them (and I envy the network manager doing the actual setup even less).
 Naturally, we need to provide a way for authorized users and services to access the devices remotely over the internet, and we've done that by offering PPTP ( Point-to-Point Tunneling Protocol )"dial-up" and IPsec ( IP Security ) "site-to-site" ( Virtual Private Networks ) VPNs. With PPTP , individual users or servers can initiate a VPN and traffic to the devices no matter what their own internet connectivity on the fly. With IPsec, one or more customer sites can be linked to the devices with a private connection that is effectively up 24/7/365. I’ve been on innumerable presales engineering calls where the prospective customer has insisted that they require public IP addresses, and the only question they have for me is whether we offer static IPs, or support DDNS ( Dynamic Domain Name System ) with the dynamic IPs. It’s probably the most satisfying part of my job to explain to them about our private IP connectivity options, which typically not only are more effective and less expensive (no unsolicited bandwidth from those automated internet scans) for them, but also vastly more secure.
Naturally, we need to provide a way for authorized users and services to access the devices remotely over the internet, and we've done that by offering PPTP ( Point-to-Point Tunneling Protocol )"dial-up" and IPsec ( IP Security ) "site-to-site" ( Virtual Private Networks ) VPNs. With PPTP , individual users or servers can initiate a VPN and traffic to the devices no matter what their own internet connectivity on the fly. With IPsec, one or more customer sites can be linked to the devices with a private connection that is effectively up 24/7/365. I’ve been on innumerable presales engineering calls where the prospective customer has insisted that they require public IP addresses, and the only question they have for me is whether we offer static IPs, or support DDNS ( Dynamic Domain Name System ) with the dynamic IPs. It’s probably the most satisfying part of my job to explain to them about our private IP connectivity options, which typically not only are more effective and less expensive (no unsolicited bandwidth from those automated internet scans) for them, but also vastly more secure. To ensure that we met our customer’s requirements and the increasing market demand market for computing infrastructure to move into the cloud, we have implemented our own cloud connectivity. See Fig 1 We are now able to build secure network connectivity between any of the global MNO connections we offer and Amazon AWS and other cloud hosts. We have added a dedicated infrastructure devoted strictly to the cloud connectivity.
To ensure that we met our customer’s requirements and the increasing market demand market for computing infrastructure to move into the cloud, we have implemented our own cloud connectivity. See Fig 1 We are now able to build secure network connectivity between any of the global MNO connections we offer and Amazon AWS and other cloud hosts. We have added a dedicated infrastructure devoted strictly to the cloud connectivity.


