Next step in cybersecurity for connected alarm systems
Alarm systems are essential for the economic success of almost all sectors of European markets. Rapid technological developments and policy developments have brought new challenges for alarm systems and the alarms systems’ market. One of these challenges is the cyber security of the connected alarm systems. Euralarm members are involved in these challenges via the CENELEC Technical Committee 79 (TC 79).
Within Europe the CENELEC Technical Committee 79 (TC 79) is developing and maintaining standards for detection, alarm and monitoring systems for protection of persons and property, and for elements used in these systems. The scope includes in particular intruder and hold-up alarm systems, access control systems, periphery protection systems, combined alarm - fire alarm systems, social alarm systems, Video Surveillance systems (formally known as CCTV systems), other monitoring and surveillance systems related to security applications, as well as associated and dedicated transmission and communication systems. Its standard publications also include the services aspects, such as planning and design, engineering, installation and handover.
Cyber security of connected alarm systems
Within TC 79 one specific Working Group (WG17) focusses on the cyber security aspects of the connected alarm systems. The Working Group was originally set up in 2018 by TC79 as an ad-hoc group to address the growing concerns of cybersecurity in connected alarm systems. The scope of the activities includes all functional elements of alarm systems as mentioned above. The objectives of the Working Group are to research and collate the existing initiatives in the field of cyber security as well as develop best practice guidance related to this topic. The know-how is shared with members of TC79. Apart from the research the Working Group has already developed a set of security policies based on best practices for adoption within the connected alarm systems. Also, a cyber task group has been set up to report on important developments from cyber related regulation impacting on alarm systems.
Alarm systems
Alarm systems consists generally of devices that are located locally within supervised premises. The devices communicate together using dedicated or shared local interconnections. The system itself communicates away from the local site via a gateway, often controlled by a fire wall. For the communication, a public data communication system is often used, such as a cloud system. Many legacy systems still use analogue connectivity, e.g., PSTN or other landline (non IP) technology. The data storage and the processing may be hosted remotely or can be shared as a cloud resource. The operations, maintenance and 3rd party services are undertaken at a remote location.
Research & findings
Based on the comprehensive research of European and global initiatives, standards, and best practices the TC79 WG17 developed a database citing over four hundred standards relating to many facets of cybersecurity. The database now covers both vertical markets, such as cybersecurity aspects of power plants and automotive as well as horizontal markets such as IT systems, ICAS. Some of the standards and best practices cover principles, such as management systems and procedures while others cover techniques, such as encryption and technical functions. The Working Group decided to focus on linking the relevant standards to threats and defenses.
Accelerating activities
Another finding of the Working Group is that the EU led activities are accelerating. Two examples of this acceleration can be found in the EU Cyber Security Act and ENISA’s Cyber Security Certification Schemes. The Working Group also noted that the Joint Technical Committee 13 (JTC13) of CEN and CENELEC develops ‘homegrown’ ENs, where gaps exist, in support to EU regulations (RED, eIDAS, GDPR, NIS, etc.). These gaps need to be avoided for presumption of conformity to these regulations. The basis for this is laid among others by the IEC 62443 (Cyber security for Industrial Automation and Control Systems), the ISO 2700x family of standards helping organizations to keep information assets secure and ETSI 303645 the globally applicable standard for consumer IoT cyber security. Figure 1 shows the strategy for cyber security for industrial automation and control systems according to IEC 62443.
Figure 1: Strategy for cyber security for industrial automation and control systems.
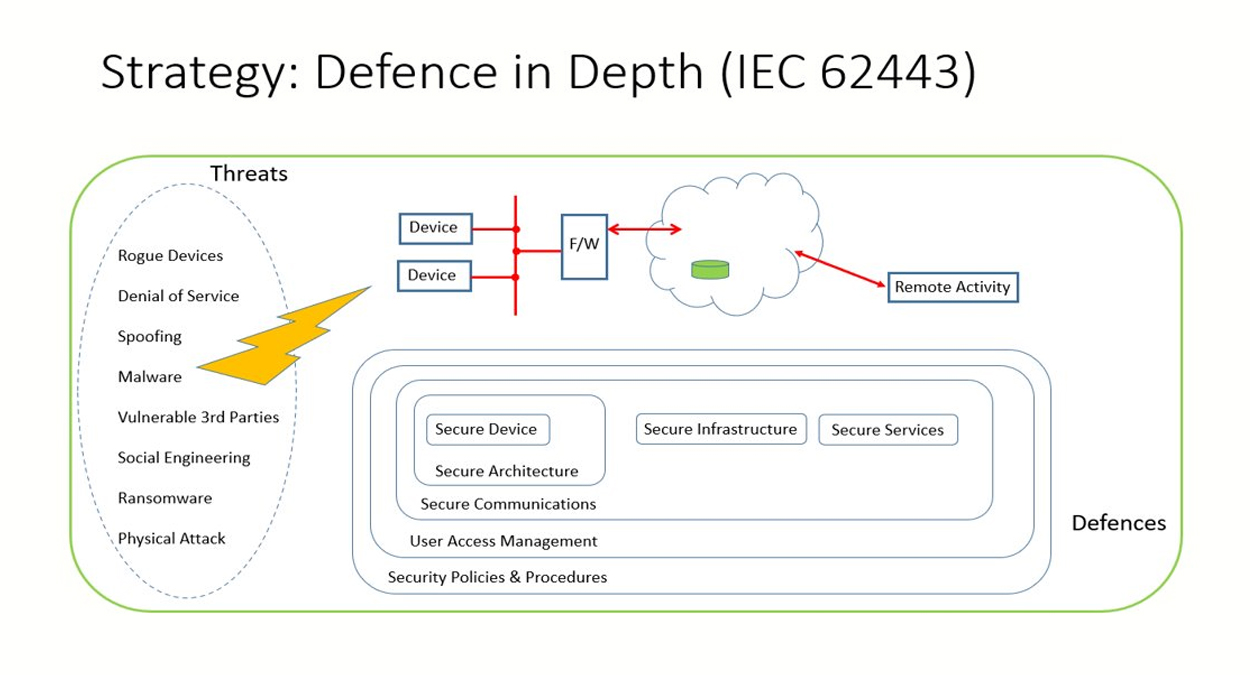
Holistic process
Based on the research and findings the Working Group concluded that cyber security is a holistic process. It also published ‘Reference Standards and Guidance on Best Practice Cyber Security for Alarm Systems’. This best practice document, of which the second edition was released last June, provides a summary of cyber security topics and standards that are relevant to alarm systems.
With over sixty pages in the guide, the Working Group felt the need to simplify the document for each of the audiences. Among these are manufacturers, designers, integrators, and MARC’s. To simplify the document the Working Group used the Taxonomy pillars that were presented in the brochure ‘Cybersecurity – Threat or Opportunity’ that Euralarm and CoESS published in 2019 (see fig. 2). For each of these Taxonomy pillar flow diagrams are being developed
Figure 2: Taxonomy pillars
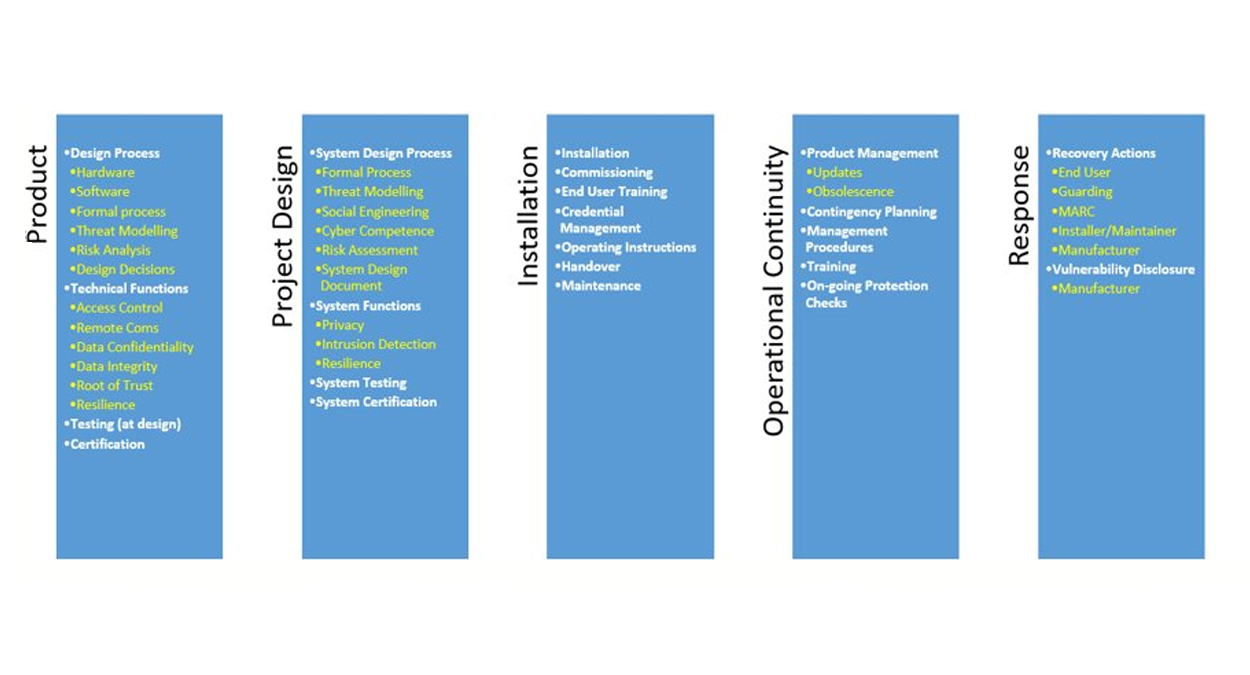
Dedicated Cyber task group
Also, a dedicated Cyber task group was created within the Working Group. This task group shares key cyber related issues impacting alarm systems, such as RED Essential Requirements impacting alarm systems and certification schemes developed by ENISA as part of the Cyber Security Act. Apart from the new task group, there is also close contact with JTC13 to consider the impact of their work and to provide input for as well as receive input from this committee to streamline the activities.
BSIA Cyber Security Product Assurance Group
Within the BSIA the activities of the Working Group on cyber security aspects of connected alarm systems have led to the launch of the Cyber Security Product Assurance Group (CySPAG). The group is made up of member companies and other stakeholders from a range of industry sub-sectors and subject matter experts who are focused on reducing the risk of product and service-related cybercrime. This interest group is actively engaged in developing industry codes of practice, guidance, certification schemes, and education to support product manufacturers, specifiers, and installers with managing their cybersecurity risks. The group endeavors to take a practical approach and recognize that there is a combined stakeholder effort in providing a cyber secure solution, i.e., it takes some effort from the manufacturers, designers, installers working in collaboration along with ongoing support and maintenance to provide a cyber secure solution.
End users also play a huge part in cybersecurity and must be made aware of their role in keeping their system secure, not only in practically managing cyber impacts on their installed system, but also in making an informed choice when selecting an appropriate company to supply, install and maintain their connected security system.
The cybersecurity landscape of risks and threats is continually evolving; therefore, the challenge is to support innovation in our industry while preventing the introduction of unacceptable risks. CySPAG’s core focus is to evaluate the cyber security landscape and develop ways in which these risks and threats can be mitigated. Likewise, initiatives are started in other European countries as well. Euralarm supports these initiatives and contributes where possible.
www.euralarm.org



